What is Covert Methods of Entry Operator Course
The Covert Methods of Entry Operator Course (CMoEO) is an extensive 3-day training program tailored for students aiming to acquire skills in physical penetration testing of facilities with different security levels. Professionals already engaged in the field who aim to refine their existing covert entry skills will find significant value in this course as well. The course is also designed for cybersecurity defenders, who are seeking to significantly enhance their competencies. It provides an exclusive opportunity to delve deep into the mindset of cyber attackers, thereby understanding their Tactics, Techniques, and Procedures (TTPs). This invaluable insight into the adversary's perspective will empower participants to architect more robust, innovative, and effective defense strategies, further fortifying their organization's physical and cyber security infrastructure.
With a focus on various attack surfaces including physical, digital, and human aspects, this training delves deeply into a wide array of topics. It includes specialized modules on lock manipulation, bypass techniques, mission planning (including reconnaissance and target evaluation), and the identification of vulnerabilities in electronic physical access control systems and other enterprise security systems.
Course Curriculum
- Roles of locks in society
- Ethics & Laws of Physical Security
- Framing the objective
- Physical Recon (remote and up close)
- Door Assessment
- How locks work
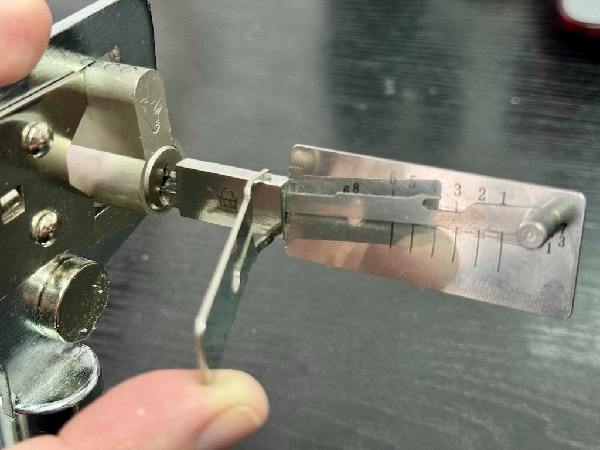
- Lock Picking
- Lock bypassing
- Decoding keys & Locks
- Field Key generation
- Door bypassing
- Window bypassing
- Essential Alarm Bypassing
- Master Keying and Keyed Alike systems
- Access Control Systems
- ID Badge cloning attacks
- PACS Reader attacks
- PACS Communication attacks
- Weaponizing Readers
- Social Engineering (OSINT, HUMINT, pretexting)
Each student will leave with a comprehensive toolkit containing everything they need to get started in this up-and-coming area of Red Teaming, Penetration Testing, and Consultancy.
Our value
In addition to acquiring essential skills for physical security engagements, this course offers numerous benefits for aspiring students:
- Expert Instruction: Learn from seasoned professionals with over 20 years of experience in information security, ensuring top-tier guidance throughout the training.
- Cutting-Edge Techniques: Stay ahead in the field with the latest methods in physical security, including remote and up-close physical reconnaissance, door assessment, bypassing, lock picking, and more.
- Comprehensive Toolkit: Each student will receive a comprehensive toolkit, equipping them with the necessary tools to excel in Red Teaming, Penetration Testing, and Consultancy.
- Real-world Applications: Gain practical insights into the roles of locks in society, ethical considerations, and the laws governing physical security, ensuring a well-rounded understanding of the subject.
- Networking Opportunities: Connect with like-minded professionals and experts in the industry, fostering valuable connections for future collaborations and career advancement.
- Career Readiness: Be prepared to enter the dynamic field of information security confidently, armed with the knowledge and skills demanded by employers in this rapidly evolving landscape.
Covert Methods of Entry Operator Course
Learn the strategies for accessing secured places covertly, all within legal, safe, and professional boundaries.
€2,750
- 3 days
- on site in Prague, Czechia
- toolkit to take-away included
Dates available:
- 4. - 6. 3. 2026
- 15. - 17. 7. 2026
- 5. - 7. 10. 2026
Sign-up for a class
Secure your spot on our immersive 3-day CMoE course.
Sign-up for a 3-day CMoE course



Other Courses
CMoE Expert Course
Operate smarter. Move quieter. Stay undetected. This is where theory becomes instinct.
PACS Bypass Course
Discover the weaknesses of the ubiqitous physical access systems and acquire the skills to exploit them.
